Mahim bizman loses Rs 1.86 crore in six late-night missed calls
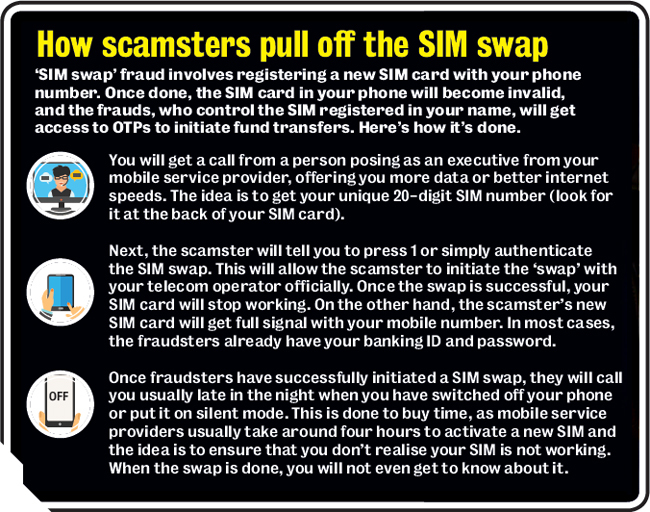
‘SIM swap’ is the latest technique to cheat mobile users
The victim received the calls on the intervening night of Dec 27-28, after which his SIM was deactivated. The hackers had obtained a new SIM in his name to transfer money to 14 accounts across the country.
In the intervening night of December 27-28, between 11 pm and 2 am, a businessman in Mahim received six missed calls on his mobile phone from two numbers, including one showing the United Kingdom dialling code +44. In the morning when he tried to dial the numbers, he realised his SIM card had stopped functioning. He was told by the mobile service provider that the SIM was de-activated based on his own request for a new SIM.
Having made no such request and suspecting that he may have become a victim of fraud, the businessman, who only identified himself as V Shah, rushed to his bank to find Rs 1.86 crore siphoned out of his company’s account, details of which were linked to his phone.
He was told that the money was transferred to 14 accounts across the country through 28 transactions. The bank was able to retrieve Rs 20 lakh, but the rest of the money was withdrawn by then.
Almost a week into the incident, Shah, who runs a textile firm, still cannot believe someone was able to empty his account through just missed calls. “My company’s bank account is linked to my mobile phone, but never in my wildest of dreams did I imagine that the cheats will empty out my account with such ridiculous ease,” Shah said.
Prima facie investigation revealed the fraudsters had managed to ‘clone’ Shah’s SIM.
The BKC Cyber Crime Police Station has filed a first information report (FIR) under the Indian Penal Code sections 420 (cheating), 419 (impersonation) and 34 (criminal act done by several people in furtherance of common intention) and sections 43 (damage to computer system) and 66D (impersonation) of the Information Technology Act.
WHAT EXACTLY HAPPENED
Preliminary investigation revealed that Shah was targeted by ‘SIM swap’ fraudsters ( see box below). “We suspect the scamsters had access to Shah’s unique SIM number and had initiated SIM Swap. To ensure he doesn’t suspect anything, they called him late in the night, when his phone was on the silent mode,” an officer from the BKC Cyber Crime Police Station said.
As per Shah’s mobile service provider, the request for SIM replacement was received around 11.15 pm on December 27.
While Shah said that he hadn’t shared his unique SIM number with anyone, nor did he recall receiving any calls asking for it, the police said the hackers could have obtained this data using malware. “Even when you happen to open a fake version of your bank website, your details are automatically compromised. Your data is accessed by scamsters every time you access unsecured Web connections, or open phishing emails. We suspect Shah may have accessed one such email or app,” the officer said.
The police cited the example of a Ghatkopar firm which lost Rs 50 lakh after fraudsters cloned the mobile number of the firm’s accountant (‘Mumbai firm duped of Rs 50 lakh in SIM swap fraud’, MM, September 26). In that case, the network of the accountant’s phone disappeared for two days, and that being a weekend, he did not realise it.
Advocate Prashant Mali, who practices in the Bombay High Court and specialises in handling cyber crime cases, said the onus to prevent SIM swap fraud lies with the mobile phone operators. “Maybe there are a few rogue elements working for telcos. I have been noticing such cases from 2011and nothing is being done to warn people,” he said.